Best Practice Guidelines: Healthcare Practice Management & POPIA Compliance Framework
Best Practice Guidelines: Healthcare Practice Management
&
POPIA Compliance Framework
Copyright © 2021 GoodX Software. All rights reserved.
GoodX online Learning Centre
learning.goodx.co.za
1. Introduction to GoodX Software
1.3. Configuration, Onboarding & Authentication
This chapter is meant to be read by:
- new clients of GoodX who
- are starting a new practice or business;
- move their practice or business from another software system to GoodX Software; and
- existing clients of GoodX who implement new features into their workflow.
1. Some notes to new clients
Client onboarding is the process of assisting you as our new client to bring your practice onto our software and ensure that you understand the services available to you.This chapter will provide information so that:
- The practice can implement proper change management strategies so that the onboarding can be successful;
- The practice will know which information to provide GoodX during the practice analysis so that GoodX can configure the software to meet the practice or business's custom needs.
2. Some notes to existing Clients - Embracing new technology to optimise practice management
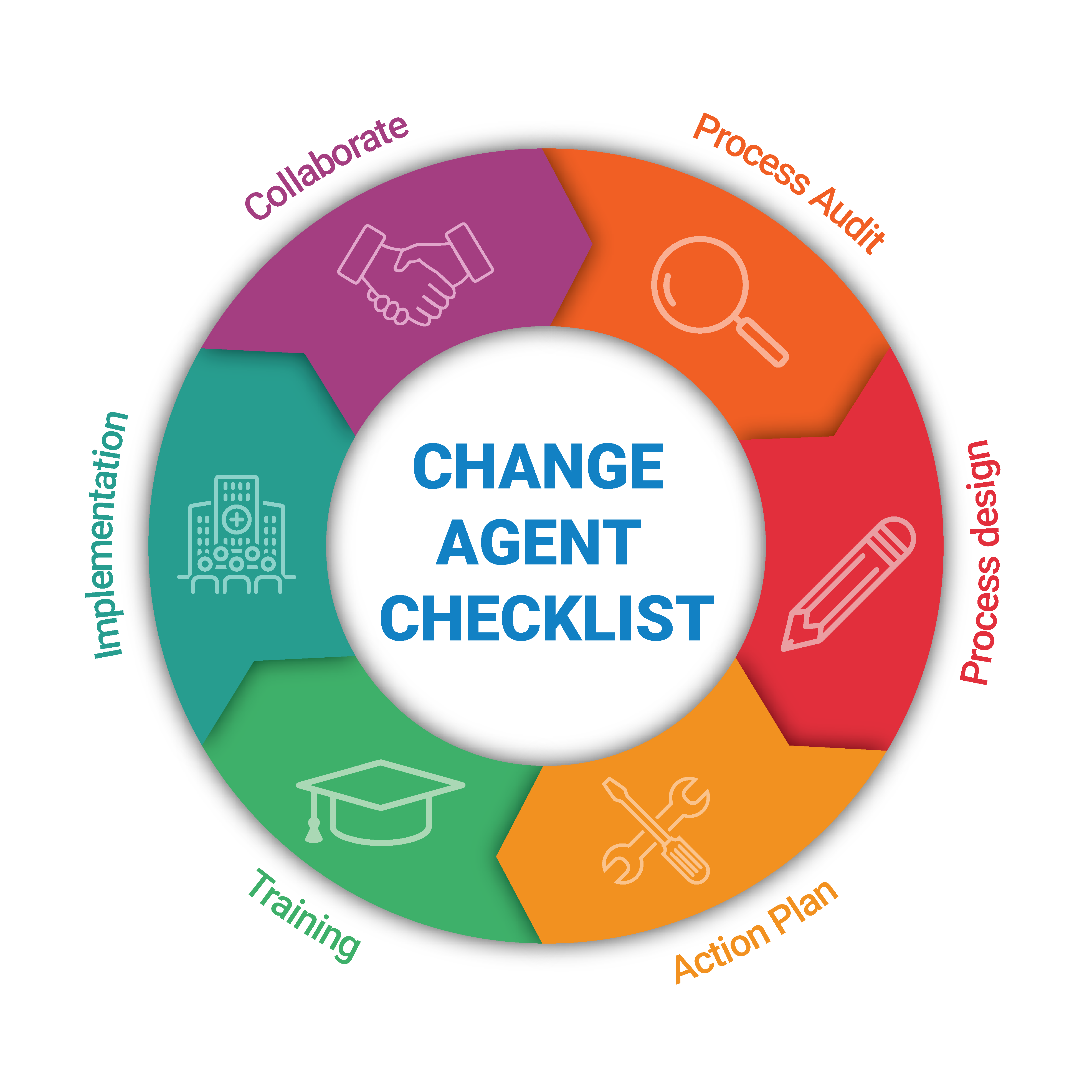 An active pursuit of systematic implementation of new technology will significantly enhance practice management.
An active pursuit of systematic implementation of new technology will significantly enhance practice management.
When choosing new software, the healthcare practice is usually very keen to implement all the bells and whistles of the software, immediately having the benefit of all the great new features that prompted the practitioner to obtain the software in the first place. However, as the years continue, if new software features get overlooked, the practice can find itself in a situation where the management of the practice becomes unnecessarily tedious.
As practices grow, more and more work needs to be done by fewer hands, and essential tasks, such as managing outstanding debts, get placed on the back burner. As a result, higher overheads and lack of proper resource management often lead to loss of income that the practice could have used to further its endeavours.
More and more practices are moving towards a paperless environment, which has the benefit of using fewer storage facilities, working from any place at any time, and reducing the risk of information loss or unauthorised access. In addition, human error as a result of data duplication or sloppy administration is eliminated.
The wins and challenges of new feature implementation
GoodX always continues to develop their software and make new features available to keep up with the times. There are a lot of wins as a result of development. New features are developed to make the practice management easier and more efficient, leaving staff to get more work done more accurately. This often results in cost savings and the reduction of risks.
Unfortunately, the elephant in the room also needs to be addressed. There are not only wins but also teething problems with the continued development and implementation of new features. For example, it can lead to slower work performance at the beginning of implementation or create bugs that strain the standard workflow and create frustration. This reality sometimes produces the unwillingness on the part of the practice to embrace change.
Change management strategies
Practices will do well to adopt well-planned change management strategies so that their practice management will not become stale and outdated.
Firstly, all stakeholders, including owners and personnel, should collaborate on how they want to move forward and what could benefit the practice as a whole. When the personnel are on board with continuous incremental improvement, it will avoid sabotage of the process and provide job security in people’s minds. It is incredulous that personnel would stop progress because of a fear of losing their jobs since if their time is spent better, they would have the ability to complete those tasks that they put on the back burner.
Secondly, a process audit should be conducted so that the current processes can be evaluated and new opportunities for optimisation can be recognised. New process design will be an aid in the implementation process. For example, investigate
- who does what and are there overlaps in the tasks between different role players?
- which processes manual that could be automated?
- which paperwork can be digitised?
- which communication channels can be optimised?
- how can the practice cut down on administrative tasks that could be improved or automated?
The list goes on.
Thirdly, an action plan should be designed in terms of which the practice
- can provide proper training to employees so that the new processes can be implemented without too much strain on the workflow;
- can work with GoodX to identify and implement changes; and
- a continued effort of improvement can be sustained.
The desired outcome
Once change management and optimisation become the new culture in the practice, the benefits will be huge.
There will be extra time to finish the tasks that are crucial but not always urgent. Personnel will experience less stress in the workplace since tedious tasks like duplication of information will be eliminated. The practice can implement better security to protect personal information, and healthcare information will become accessible to practitioners wherever their work leads them, be it a clinic or home office.
The practice will also experience a reduction of costs since the roles in the practice can be optimised, and stationary and storage costs can be reduced or eliminated. No business wants to carry unnecessary expenses, and using the software to the full will, in the long run, open up resources that can be used to grow the practice.
Conclusion
Every healthcare practice should embrace change and manage it well so that future endeavours can be undertaken with less stress, fewer costs and less frustration. However, if change seems like more effort, let the final outcome of lightweight practice management move you toward the necessary change and allow you to focus on what is really important - your patients.
Stay abreast with GoodX's new technology and features by regularly visiting the GoodX Learning Centre and taking note of the updates and additions.
Database & Applications
The GoodX software product consists of a database with two different software applications/front-ends, namely:
- the Web App; AND
- the Desktop App.
Hosting
The database can be installed on two types of hosting environments, namely:
- a local server; or
- the GoodX cloud server.
We trust that your practice will fully use all the functions available in GoodX to reap all the benefits.
Onboarding & Change Management
The prospect of working on a new system can be daunting for personnel who have either never worked on a medical software system or those who are accustomed to working on other software. Often processes within the practice or business are built around the way software functions, and these processes need to be re-evaluated and optimised. New practices need to think through the required business processes. The critical business process diagrams read together with this best practice manual can guide the design of the necessary processes.
All personnel must be involved and optimistic about the onboarding process. The person who performs the role of practice manager takes control as the change agent. If personnel are not involved and supportive of the process, the onboarding
can fail.
The change agent:
- should make sure that all personnel know of the transition to the new software and are optimistic about the change;
- should evaluate and document all processes in the practice so that amendments can be efficiently designed and communicated to all personnel;
- must be the one providing instructions to GoodX about the configuration, process design and support requests.
Onboarding consists of the following stages:

- Docs & Fees: Completing the GoodX Standard Licence Agreement, completing all install documents and paying the install fee.
- Collaborate with all personnel to get everyone involved in the changeover.
- Evaluate and design business processes based on the new software functionality.
- Completing a practice analysis with the practice manager to obtain all necessary information to configure the software for the needs of the practice/business.
- Installation and configuration of the software.
- Personnel receive training on the new software and continue learning via the online Learning Centre.
- On-site installation & onboarding by GoodX personnel to:
- install RDP's and correct internet browsers;
- make sure all users have the proper access to the software;
- assist the practice manager to either implement new work processes or to make any necessary changes to establish optimal work processes;
- assist users in customising the software according to their user preferences;
- check that personnel use the software correctly;
- help personnel to implement their training knowledge with the use of the software;
- to quality ensure the installation and application of the training.
Onboarding schedule:
A typical onboarding schedule will look like this: (Stock management & Accounting management onboarding will each have different schedules.)
| Date | Onboarding Stage | GoodX Department(s) involved |
|---|---|---|
| Before Go Live Date | Sign Contract, Install Fee Payment & Completion of Documents | Marketing |
| Before Go Live Date | Practice Analysis for custom configuration | Onboarding |
| Before Go Live Date | Install & Database Configuration | Technical |
| Before Go Live Date | Fundamental Training:
|
Onboarding |
| Go Live Date * |
On-site Installation & Onboarding (Assistance) | Onboarding |
| After Go-Live Date | Support by Client Liaison: help@goodx.co.za |
Support |
Software Configuration based on the Practice Analysis
A training & onboarding team member will contact the practice for a practice analysis. The outcome that needs to be achieved is that GoodX will be able to properly configure the software for the needs of the practice and be in a position to properly prepare for the onboarding of the practice with the go-live month.
Some of the information that will be required will be:
- The layout of the practice
- The patient movement through the practice and workflow of the employees
- The demographic details of the practice
- VAT & Banking details
- Who the users are and which roles do they perform in the practice
- Key points in the practice
- The medical price lists used by the practice
- Which medical aid contracts the practice has signed
- If demographic patient data needs to be imported
- If the practice will be using the accounting management module:
- A list of the ledgers from the accountant
- Opening balances for the trial balance
- Cashbook setup (all bank accounts as well as the petty cash account)
- List of every entity/practice number’s creditors
- Opening balances of the creditors
- If the practice will be using the stock management module:
- The counting locations that the wants GoodX to configure for the stock (places where the stock is kept);
- The stock list is divided into counting locations (e.g. code, description, Nappi code, pack size, price and counting location (places where the stock is kept Consultation room – cupboard 1 – drawer 1)
- Which stock items should be marked as non-chargeables?
- Which stock items should be marked as non-stock items? (Costing but without movement.)
- List of every entity/practice number’s creditors
- Opening balances of the creditors
Authentication
Various user authentication technologies are in high demand for both online and desktop software and services. Healthcare practices must recognise that passwords are not the only way of authenticating users. There are various authentication mechanisms available to enhance security when users access information in the practice.
The traditional username and password authentication method is a single security layer. However, usernames are often easy to discover, as users often utilise readily available information, like email addresses or birthdays, as their passwords. Furthermore, passwords are often difficult to remember, so people choose easy ones or use the same password across many platforms.
That is why almost all service providers like banks, social media platforms and medical software providers have added additional security layers to accounts. Users could access their software or account settings and activate multi-factor authentication.
What is Multi-Factor Authentication?
Authentication is the process of confirming the identity of a person, device, or entity attempting to access data, resources or applications. Validating identity establishes a trust relationship for further interactions and access.
There are various authentication methods whereby a user is granted access only after successfully presenting one or more pieces of evidence (factors) to an authentication mechanism. Multi-factor authentication (MFA) is a security mechanism that requires more than one verification method to validate a user's identity. MFA thus creates a few layers of defence that makes it more difficult for an unauthorised person to access a location, device, network or database.
Three categories of factors
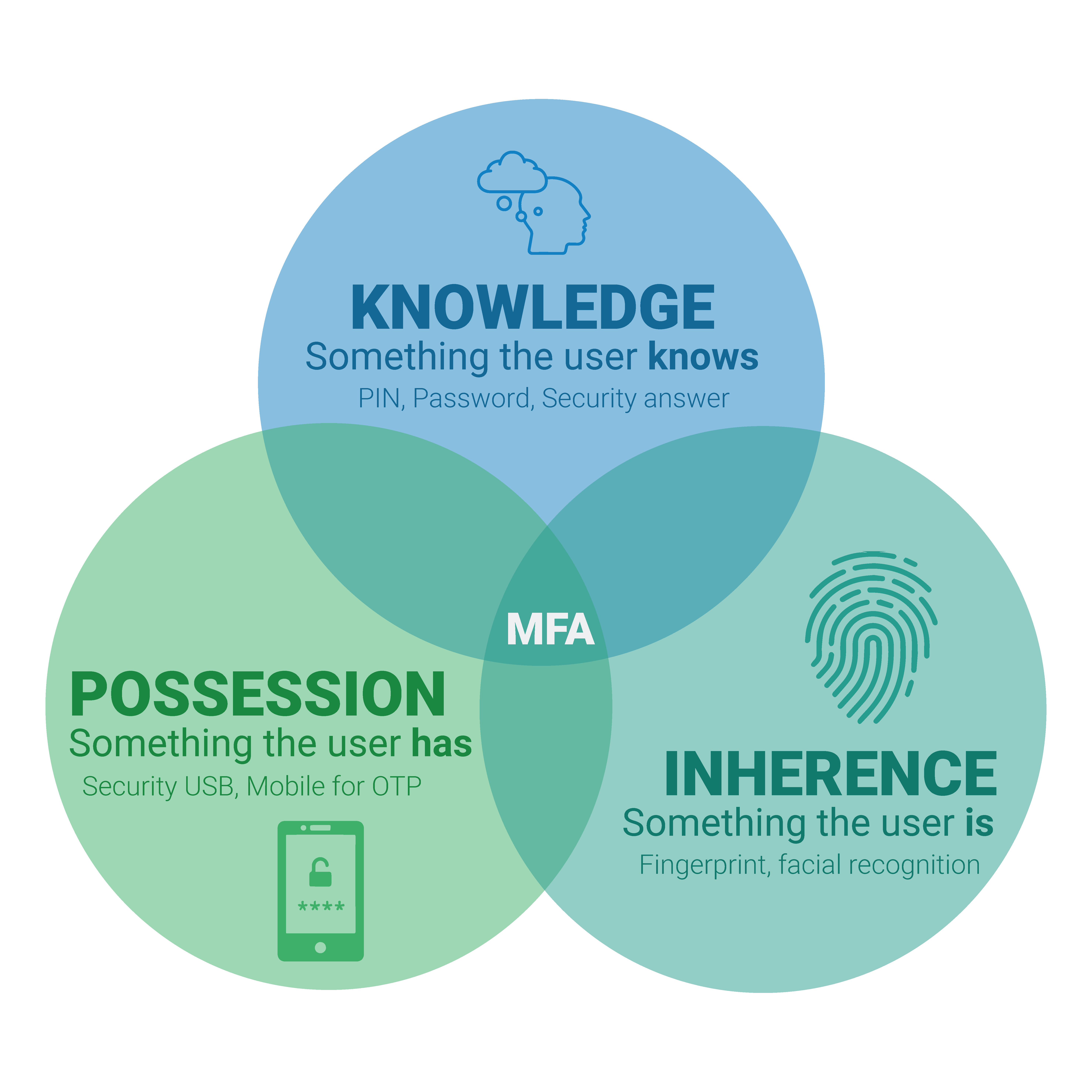 The most commonly used factors fall into one of these three categories:
The most commonly used factors fall into one of these three categories:
- Knowledge is something the user knows, like a personal identification number (PIN), a password or the answer to a secret question.
- Possession is something the user has, like a security USB key fob or a mobile phone used to accept a text message or run an authentication app that can generate a one-time password (OTP).
- Inherence is something the user is, which can be any form of biometric identification, like fingerprints and facial recognition.
It is essential to make use of factors from different categories. For example, thieves may steal a password, but they cannot easily steal a fingerprint.
Benefits of Multi-Factor Authentication
- Multi-factor authentication increases security with third parties and organisations. Adding another form of authentication — mobile, biometric, or physical — creates a layered defence.
- MFA controls who has access to files. Instead of using just passwords, which can be passed around or duplicated, multi-factor authentication restricts access to authorised users only.
- It eliminates password risks. As long as passwords have been in existence, they have been cracked or guessed. Over 65% of accounts use duplicated passwords, so if an unauthorised person finds the password for an employee's email account, there is a 65% chance they have access to other sensitive information deeper in the network. Best practice requires the use of unique and complex passwords, used with multi-factor authentication.
Multi-Factor Authentication within GoodX Web
The following outline presents the factors by category that GoodX Web utilises to enhance security and access control:
- Knowledge (something you know):
- Passwords: a password is required to log into the software, which password should be changed regularly.
- Pin: a pin is required to populate the practitioner's signature on clinical events.
- Possession (something you have):
- Pushnotify: send a notification to a device, such as a computer or a smartphone, asking it to accept a login request.
- Userfob: a USB key must be presented before attempting to log in.
- Inherence (something you are):
- Facial recognition - an image is saved to the user's profile and compared to the current facial structure to accept a login request. Facial recognition technology is used in conjunction with a Stationfob to verify a station in a secured location, reducing the risk of using a social media image. It is typically used at a nurses station or similar setting where only authorised personnel are allowed.
Authentication technology is constantly evolving. As a result, businesses must look beyond passwords and consider authentication to improve security and user experience. Using multi-factor authentication is one of the easiest ways to prevent unauthorised users from accessing confidential information and therefore protecting the business against legal claims and fines.
GoodX provides different types of login details. A practice and users could typically receive the following information:
|
Web App |
GoodX Cloud |
Desktop App |
Learning Centre |
Client Portal | |
|---|---|---|---|---|---|
| URL |
Unique URL provided to each practice | RDP icon on your desktop | None |
learning.goodx.co.za | client-portal.quantsolutions.co.za/login |
| Username |
Per user | Created on each computer | Per user | One login per practice NB Case sensitive! |
Email address of User * |
| Password |
Per user | Per user | Per user | NB Case sensitive! |
Chosen by the User |
Please take note:
- * Only Users added as Contacts to the GoodX Install in the GoodX Management System will be able to register on the Client Portal.
- Please make sure that you use the correct Login details for the correct application. Your FCL will assist you if you are unsure.
-
All access to the software is connected to the user. The access control will be linked to the username.
** Beware: Never reveal your password to anybody. The system keeps an audit trail of all changes made in the system. If your user account is used for unauthorised changes, you will be held liable for those changes. If your password is compromised, change the password as soon as possible.