Best Practice Guidelines: Healthcare Practice Management & POPIA Compliance Framework
Best Practice Guidelines: Healthcare Practice Management
&
POPIA Compliance Framework
Copyright © 2021 GoodX Software. All rights reserved.
GoodX online Learning Centre
learning.goodx.co.za
4. Diary Administration: Roles & Purpose
4.2. POPIA tips for Diary Administration
These are some tips for POPIA compliance in Diary Administration
The information is based on the POPIA Action Maps, a checklist for practices to assist in implementing the POPIA requirements.
![]()
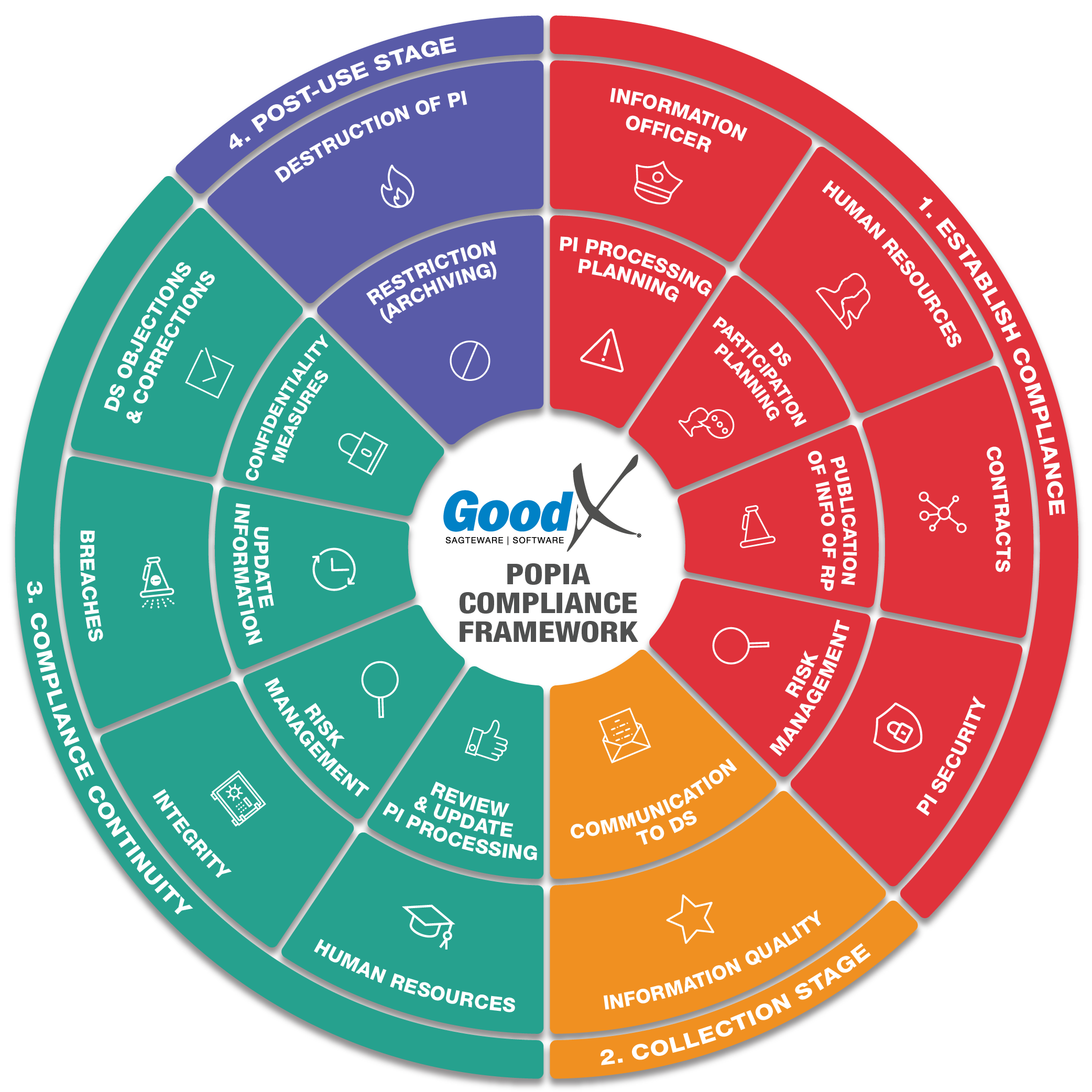
Stage 1: Establish Compliance |
 |
PI Security
|
|---|---|---|
 |
PI Processing Planning
|
|
 |
DS Participation Planning
|
|
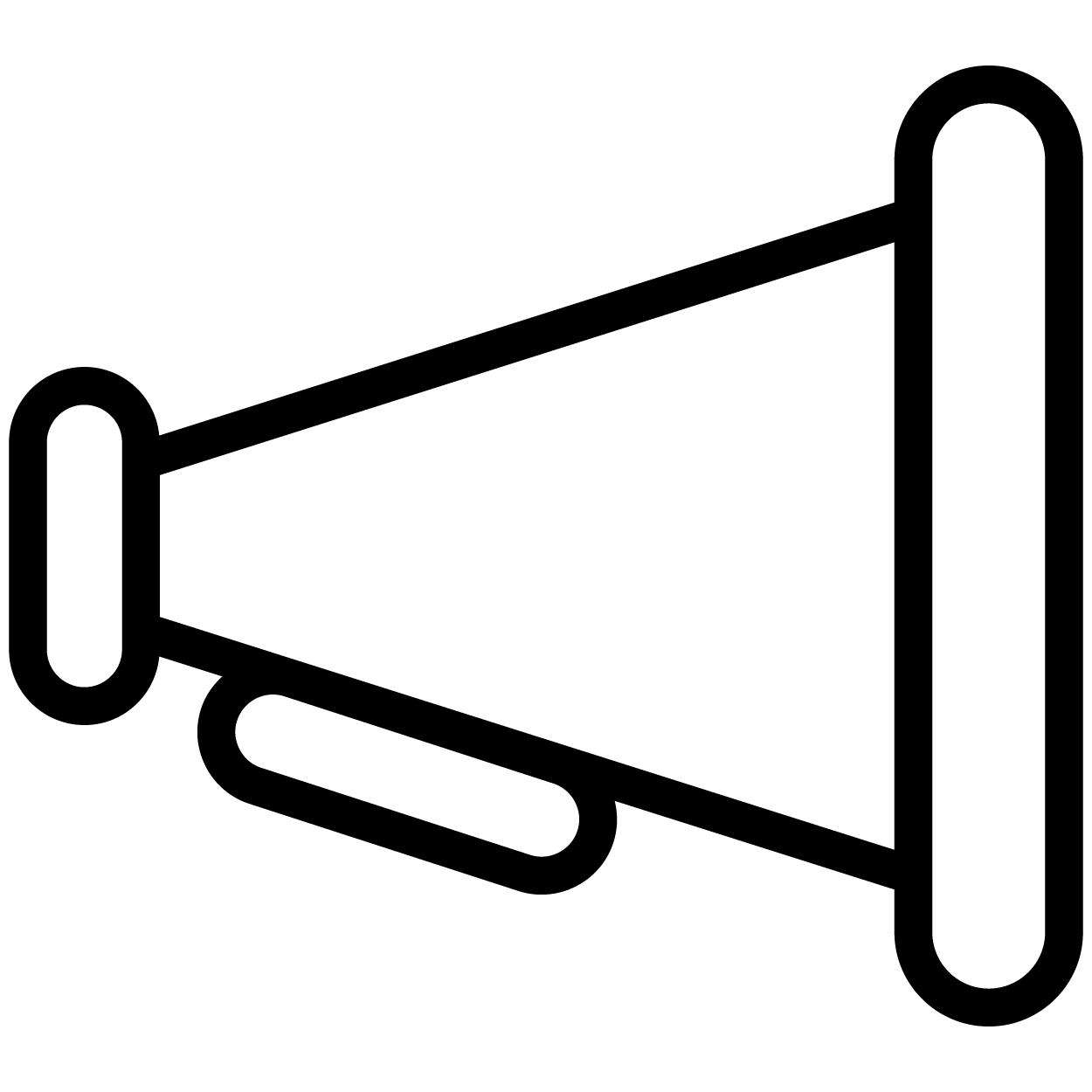 |
Publication of information of the practice (RP)
|
|
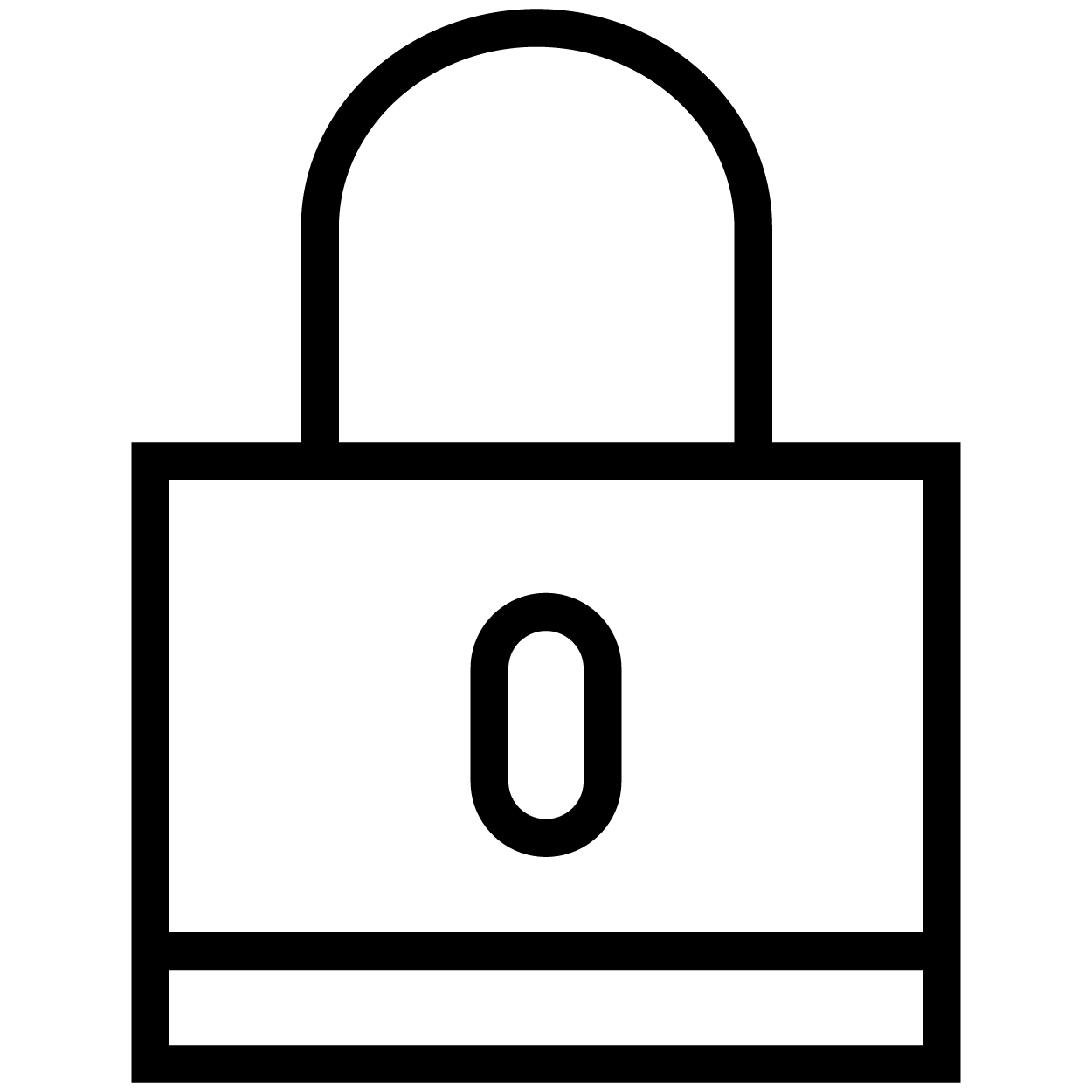
Stage 3: Compliance Continuity |
 |
Confidentiality Measures
|
 |
Updated Information
|
Examples
Please take note: should you wish to use this information, you should adapt it to your practice's needs.
Example of a clean desk policy
- Every employee is responsible for protecting the confidentiality of personal and special personal information of the practice, colleagues, and patients.
- No confidential information may be left on a desk or other place in the employee's absence, no matter how short the absence is.
- Computers and software must be locked when an employee leaves the computer.
- Personal mobile devices in a healthcare practice reception should be discouraged.
- Physical documents must be kept safe to ensure that unauthorised persons cannot access the documents.
- No documents containing confidential information may be thrown into rubbish bins where unauthorised persons can access that information. Documents must be destroyed by shredding or the practice's authorised waste removers.
- Documents that do not contain confidential information may be disposed of in the recycling bins.
- All confidential information lying around unsupervised must be reported to the practice manager. The practice manager must ensure that those documents are gathered for safekeeping.
- Documents may only be taken home or generated at an employee's home, with the practice manager or practitioner's written consent.
- No confidential documents or documents containing confidential information may be thrown away at an employee's home. It must be shredded at the office or disposed of through the practice's authorised waste removal contractor.
- Hard copy documents should be avoided by using electronic form filling mechanisms.
Example of a password policy
- Keep your passwords safe and do not share your passwords with any other persons.
- Never use the password of someone else, even if you have consent to use it. If you don't have access to software, you should first enquire from the practice manager/practitioner if you are allowed access and if yes, request your own login.
- Do not document your passwords where third parties can get access to the passwords.
- Passwords should preferably be a sentence that can easily be remembered.
- Passwords should be at least 14 characters long.
- Weak passwords typically contain the following:
- Less than 14 characters;
- A lack of different types of characters;
- Personal information;
- User-specific information.