An introduction to the protection of personal information in the healthcare practice
1. Privacy in South Africa
Topics
- What is privacy?
- How is privacy infringed?
- How is privacy protected?
- Common law
- The constitution
- Other legislation
- Codes of conduct - the HPCSA ethical rules
- The protection of personal information act (POPIA)
- Why care about knowing all about POPIA?
- Mitigation of damages
- Benefits
- Abbreviations.
1. What is privacy?
One of the big questions to ask oneself is: “What is privacy?”
"Privacy can be defined as an individual condition of life characterised by seclusion from the public and publicity. This condition embraces all those personal facts which the person concerned has himself determined to be excluded from the knowledge of outsiders and in respect of which he has the will that they be kept private."
Neethling’s Law of Personality 2005 50
2. How is privacy infringed?
Infringement is committed by
- intrusion into the private sphere of individuals, e.g.
- Reading of private documents
- Sending unsolicited communication
- disclosure of private information, which is information pertinent to the private domain which a DS wishes to be kept private, e.g.
- Sharing information about a patient's health and wellbeing
- Disclosing facts which have been wrongfully obtained
3. How is privacy protected?
The healthcare industry is in possession of a lot of sensitive and confidential Personal Information (PI) of patients and so healthcare practitioners have a huge responsibility towards patients to keep that information safe. Practitioners are used to keeping such PI confidential, as the ethical rules of the HPCSA and other legislation deals with patient confidentiality.
There are however other relationships that the practice also has to consider as falling under the provisions of the POPIA.
South Africa has always protected the right to privacy by:
3.1. Common law
The Common law has always protected the right to privacy by means of the law of delict. (Personality rights = Right to body, life, physical liberty, a good name, dignity, feelings, privacy, identity.)
3.2. The Constitution
Section 14 of the Constitution of South Africa protects the right to privacy.
3.3. Other legislation
Examples would be:
Children’s Act 38 of 2005
13. Information on health care
13. (1) Every child has the right to -
(a) have access to information on health promotion and the prevention and treatment of ill-health and disease, sexuality and reproduction;
(b) have access to information regarding his or her health status;
(c) have access to information regarding the causes and treatment of his or her health status; and
(4 confidentiality regarding his or her health status and the health status of a parent, care-giver or family member, except when maintaining such confidentiality is not in the best interests of the child.
( 2 ) Information provided to children in terms of this subsection must be relevant and must be in a format accessible to children, giving due consideration to the needs of disabled children.
Choice on Termination of Pregnancy Act 92 of 1996
5 Consent
(3) In the case of a pregnant minor, a medical practitioner or a registered midwife, as the case may be, shall advise such minor to consult with her parents, guardian, family members or friends before the pregnancy is terminated: Provided that the termination of the pregnancy shall not be denied because such minor chooses not to consult them.
Disaster Management Act 52 of 2002
- Forced screening & testing allowed without consent of DS
- Contact tracing regulations ito the act allow for limitation of privacy rights e.g. the tracing database.
The Electronic Communications and Transactions Act 25 of 2002
- Prohibits the unauthorised access to or interception of information
- Prevents unauthorised intentional interference resulting in modification, rendering ineffective or destruction of information - for instance computer viruses,
- Prevents the overcoming of security measures which protect data, Computer related fraud, forgery and extortion, for example hackers that plant Ransomware and keep a practice’s data at ransom.
3.4. Codes of conduct - the HPCSA ethical rules
Core ethical value nr 8 speaks specifically to Confidentiality between practitioners and patients in saying “Health care practitioners should treat personal or private information as confidential in professional relationships with patients - unless overriding reasons confer a moral or legal right to disclosure.”
BOOKLET 1:
5.3 INFORMED CONSENT
Health care practitioners should:
5.3.1 Give their patients the information they ask for or need about their condition, its treatment and prognosis.
5.3.2 Give information to their patients in the way they can best understand it. The information must be given in a language that the patient understands and in a manner that takes into account the patient’s level of literacy, understanding, values and belief systems.
5.3.3 Refrain from withholding from their patients any information, investigation, treatment or procedure the health care practitioner knows would be in the patient’s best interests.
5.3.4 Apply the principle of informed consent as an on-going process
5.3.5 Allow patients access to their medical records
For detailed information consult the HPCSA Ethical Booklet on Informed Consent
5.4 PATIENT CONFIDENTIALITY
Health care practitioners should:
5.4.1 Recognise the right of patients to expect that health care practitioners will not disclose any personal and confidential information they acquire in the course of their professional duties, unless the disclosure thereof is:
- made in accordance with patient’s consent;
- made in accordance with the court order to that effect;
- required by law; or
- in the interest of the patient.
5.4.2 Not breach confidentiality without sound reason and without the knowledge of their patients
5.4.3 When claiming from medical schemes explain to patients the significance of ICD-10 coding and get the permission of patients to breach confidentiality when making a medical scheme claim.
3.5. The Protection of Personal Information Act 4 of 2013 (POPIA)
Personal Information is a valuable commodity and it has become more and more difficult for individuals to retain autonomy over their private information.
The POPIA has been signed into law on 13 November 2013. On 1 July 2020 the provisions were promulgated (put into effect) and all persons or companies coming into contact with personal data have one year to become compliant with the provisions of the act.
The questions to ask about the POPIA is:
1. What does the POPIA require?
2. How do we implement the provisions of the POPIA, since the act provides lots of principles, but no specific examples and we don’t yet have a body of case law to understand how the principles will be applied by the South African courts.
In drafting the POPIA, our legislator used the predecessor of the European General Data Protection Regulation 2016/679 (EU) or GDPR, as a template, thus making its provisions on par with international law. There are obviously some differences between these bodies of legislation, but the general principles are the same and it helps us in South Africa to be able to see how other countries have implemented the GDPR so that we can implement the POPIA provisions here in South Africa.
Take note: care must be taken not to indiscriminately implement the practical applications of the GDPR into our South African circumstances, as the legal instruments differ in some ways.
4. Why care about knowing all about POPIA?
1. Mitigation of damages
The practice can suffer many kinds of damages, of which the least are the fines prescribed in the POPIA.
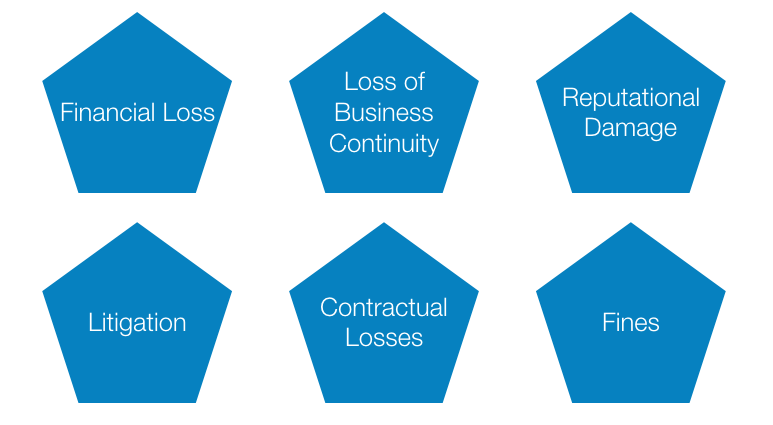
Examples of these damages can be:
- Financial loss due to e.g. unplanned expenses for updated IT security
- Loss of Business continuity due to e.g. loss of patient data;
- Reputational damages, which is loss of goodwill, due to patients bad mouthing the practice;
- Litigation that is time consuming and might result in more financial loss;
- Contractual losses due to clients cancelling contracts with the practice or never returning to the practice
- Lastly the fines that can be incurred from the IR - which is actually not a big risk if the practice co-operates with the IR after a security breach.
2. Benefits

Examples of benefits are:
- Compliance provides a means for the practice to reassess old practices and processes. The practice can save operational costs when processing of PI is researched and streamlined, which often cuts out unnecessary processing and work.
- Being compliant obviously reduces legal risk, therefore leading to further cost saving.
- When clients and patients feel confident in the way the practice is handling their PI, the chances of word of mouth marketing by patients and the retainer of clients and patients are huge.
5. Abbreviations
The following abbreviations will be used in this guidelines book:
|
POPIA |
Protection of Personal Information Act 4 of 2013 |
| PAIA | Promotion of Access to Information Act 2 of 2000 |
|
PI |
Personal Information |
|
SPI |
Special Personal Information |
|
RP |
Responsible Party |
|
DS |
Data Subject |
|
CP |
Competent Person |
|
IR |
Information Regulator (State) |
|
IO |
Information Officer (Private) |
| DIO | Deputy Information Officer |
|
LIA |
Legitimate Interest Assessment |
|
PIIA |
Personal Information Impact Assessment |