Best Practice Guidelines: Healthcare Management Internal Controls
Best Practice Guidelines: Healthcare Management Internal Controls
Copyright © 2020 GoodX Software. All rights reserved.
GoodX online Learning Centre
learning.goodx.co.za
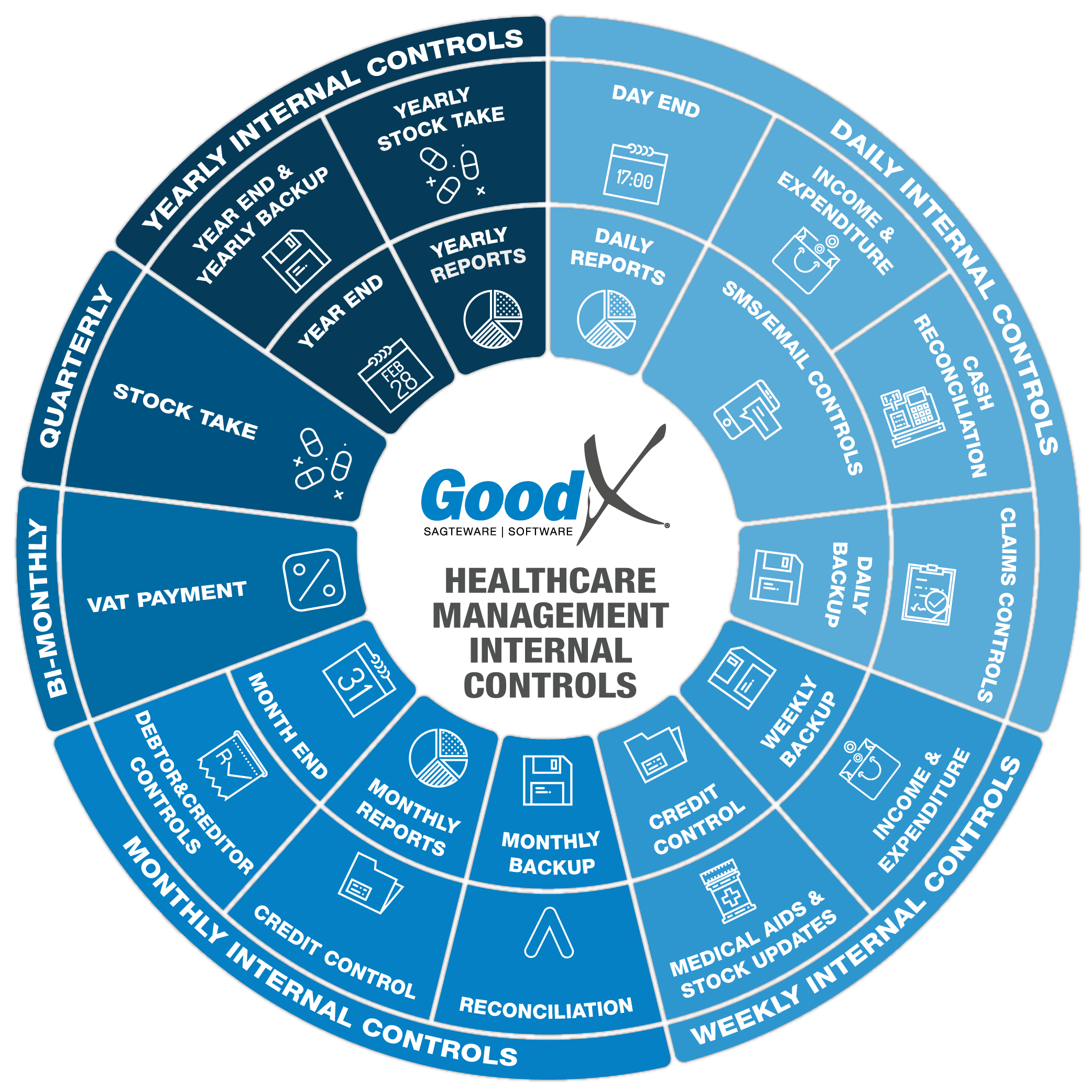
2. Daily Internal Controls Summary
2.7. Daily Backup

DATA NOT BACKED UP = DATA NOT YET LOST
If your practice operates on your own server and does not have a proper backup regime in place, you are vulnerable to data loss due to viruses, ransomware, hardware failure, theft or fire.
The data that you collect on your software is of the utmost importance and it should be a priority for each practice to make sure that you contract an expert IT consultant to make sure that your IT is dealt with properly. It is imperative that your hardware is kept up to date and that your backup process is implemented with all due diligence.
It is the responsibility of the practice to verify the validity of backups by checking that backups were successful with no errors and confirming that backup files are present at the backup locations after every backup. If there is any indication that the backup is not successful, it is the responsibility of the practice to contact the IT company immediately to resolve the problem.
A big concern is that practices do not implement proper safety precautions for their servers, making the data especially vulnerable to viruses and ransomware. Best practice dictates that no emails should be opened on a server and proper firewall protection for your server should be implemented.
The internal controls diagram shows you that each period ends with a backup to be made of the data. Different sets of hardware should be used for the different backups, as some viruses go undetected for a while.
A good procedure is to have different hardware for:
1. Monday to Friday backups.
2. Week 1 - 4 backups.
3. Month 1- 4 backups.
4. Yearly backups.
Make independent backups i.e., to different USB devices instead of rewriting to one medium. If a virus is picked up on Week 3 of Month 2, and you notice the virus only during Week 1 of Month 4, you will at least have an uncorrupted backup from Week 2 of Month 2 and not lose all your data.
Verify backup media after making a backup by testing archives and file sizes.
It is imperative that backups be kept off-site in case of theft or fire. Leaving a backup device connected to the PC will not be of any use in such circumstances or in case of ransomware or viruses.
Take note:
The information in this chapter applies to the weekly, monthly and yearly backups as indicated on the diagram of the internal control.
Ransomware - What to do?
There is a virus called CryptoLocker being sent to email addresses. CryptoLocker is a ransomware trojan targeting computers that run on Microsoft Windows. Ransomware is a form of malicious software or ‘malware’ which demands payment to unlock your computer and can often prove difficult to clean up or remove from both PCs and Macs.
CryptoLocker is commonly spread through infected email attachments, often disguised as a PDF. This virus encrypts your files, restricting access, and holding your files 'ransom' for a certain fee. The virus threatens to delete files if this fee is not paid by a set deadline. This is something you should be careful of even if you have virus protection software installed, as it may not detect CryptoLocker.
How can you protect your data?
1. Install and regularly update anti-virus software to detect malware;
2. Regularly backup all your files to a cloud service in case your computer cannot be cleaned of the virus;
3. Inform all your staff of the risks and how to protect their data.
What to do if your computer is infected?
1. Disconnect your computer from the internet immediately;
2. Disconnect all storage devices (USBs and Hard drives);
3. Switch off your computer;
4. Contact your IT department to format the PC or restore a backup image;
5. Once you are confident that your computer is virus free and you have a backup available, please contact GoodX to reinstall your software and restore your backup.
It is your responsibility to protect your data and make sure that your data is properly backed up and that the backup is tested as reliable for a restoration process.